Just before the 2021 Fourth of July weekend, as many were preparing for long weekend getaways and cookouts, a massive coordinated cyberattack was launched against Kaseya, an IT solution provider. Because many of Kaseya’s customers are Managed Service Providers (MSPs), this attack affected thousands of organizations across the globe.
The attack was centered around Kaseya’s VSA software, a remote monitoring and management tool that helps organizations manage networks and endpoints. The hacker group found a vulnerability in the VSA software’s authentication bypass functionality and were able to circumvent authentication controls, start an authenticated session, upload a malicious payload, and execute commands. They triggered a false malicious software update that was then deployed across their entire network of their direct customers and MSP client customers. The effects were felt by a grocery store chain in Sweden, schools in New Zealand, and an entire town in Maryland. The ransom? $70 million.
This attack isn’t the first this year, in fact, it’s one of many major cyberattacks affecting entire industries and supply chains in the last few months. In early May of 2021 American oil pipeline company Colonial Pipeline experienced a Ransomware attack that forced them to temporarily shut down their pipeline, which then led to panic buying in turn causing widespread gasoline shortages in the Eastern United States. Just weeks after, JBS, the world’s largest meat producer, experienced a similar attack that forced all of their plants to shutter, halting the production of a quarter of the country’s meat supply.
IT Secure Services, an Information Technology security firm based in Manchester, NH has experienced their fair share of ransomware attacks, Founder and CEO Joerg Laves anecdotally recalls a recent event:
“Just this last year a manufacturing company reached out to us thinking there might be a hacker on the network. They thought this was true as one of their emails was recently broken into. While speaking with them we found they didn’t have anyone who managed their backups. As we began working with them the first thing we did before announcing our presence on the network was backup their servers.
An attacker on the network turned out to be true, and their email was hosted on a local exchange server. They had a lot of extremely old hardware, hardware so old that modern security agents could not be installed on them. As we began to secure the network, the hackers used the old devices to Ransom all the files on the network. Our backups had completed however, and we quickly rolled their data back & went above and beyond to remove all hacker footholds on the network.”
As large-scale cyber attacks become more and more common (they doubled from 2019 to 2020), the need for a plan to protect your organization becomes even more necessary. Understanding exactly what ransomware is and taking the steps to prevent an attack can be what allows your business to survive a ransomware attack.
What is Ransomware?
Ransomware is a specific type of malware (software designed to damage or give someone unauthorized access to a computer or network) that essentially holds that device’s files for ransom. Once an attack is deployed, the victim must pay that ransom in order to access their files, and often receive threats of permanent deletion or stolen or sold data if the ransom is not paid.
A single Ransomware attack can cause extensive financial damage. The average ransom payment is $170,404, with the most common payment being around $10,000. The cost of a Ransomware Attack is not limited to just the ransom paid, between remediation efforts, business downtime, operational costs, and more, the average cost of recovering from a Ransomware attack can be 10 times the size of the ransom payment.
Many small to mid-sized businesses can’t handle the costs associated with an attack, and may need to shut down shortly after. And because many small and mid-sized business owners don’t believe they are at risk of an attack, they don’t take action until it’s too late. And getting hit once by an attack doesn’t mean a business is in the clear, in fact, 80% of businesses that paid after a Ransomware attack got hit a second time.
How Does a Ransomware Attack Work?
Contrary to popular belief, these attacks aren’t done by lone-wolf rogue hackers as they are often portrayed in popular culture. Organizations such as REvil (who executed the Kaseya attack) or Maze are sophisticated and have a team working to choreograph multiple attacks at the same time.
A ransomware attack typically consists of three main components, software creation and hosting, distribution, and ransom collection. Hacking organizations have individuals dedicated to each of these tasks, and much like a legitimate software organization, they employ 3 common operational models.
Vertical
Many hacking organizations employ the concept of vertical integration, which is the control of a supply chain from end-to-end by a single company. This model implies that the hacking group acts much like a software company like Apple, where everything operates under a single umbrella.
In this model hacking groups manage the development of the attack, hosting, deployment, and collecting the ransom. While this model allows the organization to retain the entirety of their profits, like a legitimate organization they also face the challenge of attracting and retaining talent that can execute these attacks successfully.
Reselling
In other instances, hacking organizations will outsource their developed ransomware to other groups. This reduces the effort required by the organization and can help distribute such attacks on a larger scale.
Managed
In the world of enterprise software, Managed Service Providers purchase software wholesale and transform them into SaaS products that they sell to their customers (just like PiF does!). Hacking organizations do something similar by purchasing software from one group with a licensing fee and then go distribute it.
Most Ransomware attacks follow a specific set of steps known as a “Kill Chain”
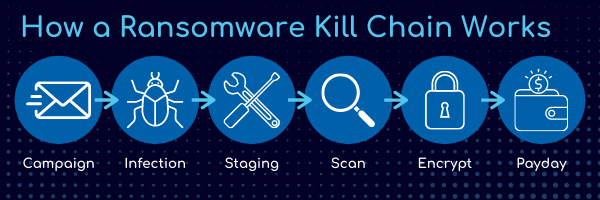
Distribution Campaign
Attackers use techniques like social engineering and weaponized websites to trick or force users to download a dropper which kicks off the infection
Malicious Code Infection
The dropper downloads an executable which installs the ransomware itself
Malicious payload staging
The ransomware sets up, embeds itself in a system, and establishes persistency to exist beyond a reboot
Scanning
The ransomware searches for content to encrypt, both on the local computer and the network accessible resources
Encryption
The discovered files are encrypted
Payday
A ransom note is generated, shown to the victim, and the hacker waits to collect on the ransom
What to do if you’re the victim of a Ransomware attack
Because Ransomware is so prevalent now, there are common best practices to ensure your business remediates this breach successfully. While IT Secure Services knows that once you’ve been ransomed it’s too late, Joerg says, “The best thing to do moving forward is get all the forensic data & call your insurance BEFORE remediating the attack. Insurance companies often require this data before paying.”
The first key step is to try to isolate the attack, take infected computers and devices off your network and any shared storage services. This will slow or stop the spread of the attack. Make sure you identify the “patient zero,” and if there’s more than one infected device repeat the same process for each.
Once you know which devices are affected, you can identify the ransomware itself. Many ransomware and hacking organizations will identify themselves (so you can pay them), this data can help you understand how it works and can help you report it to authorities easier.
Though it may seem like an easy fix, do not pay the ransom. As mentioned previously, many organizations fall victim to a second attack, and many don’t receive their files back at all. This leaves you with the choice to either remove the malware yourself or simply wipe every device and start anew.
Removing the malware isn’t a clear-cut solution, you may not be successful and time spent trying to remove the infection is more time and resources lost to your organization. Newer ransomware is designed to not be removed, and most small to mid-size organizations don’t have the IT capabilities to remediate such an attack.
The best way to rid your organization of a malware infection is to completely wipe every device and reinstall everything from backups.
Laves says the biggest mistake you can make if you’ve been attacked is pressing forward in trying to solve the issues, “without bringing in any experts to see how your network was infected. If attackers see you recovered successfully and are still present, they will do it again.”
By acting without deep knowledge and experience mediating an attack, your organization can “…cause more downtime and oftentimes they will try to encrypt the backup so you can’t roll back again.” This means you may never be able to retrieve the data you have lost.
Consulting with experts like IT Secure Services can help you bounce back from an attack quicker and with fewer losses.
How to prevent a Ransomware Attack
All organizations are at risk of an attack regardless of industry, size, or location. You may make the incorrect assumption that your business isn’t of interest to cyber criminals, but the fact is anyone can be a victim at any time. There are steps you can take to prevent an attack, and by being vigilant in enacting and maintaining cyber security standards you can keep your organization protected.
Some steps are simple, like keeping your operating system up-to-date, installing anti-virus software, and not giving permissions or installing software unless you know exactly what it is and how it works on your device.
You can also remind your employees to be safe as well by not clicking links from unknown or seemingly sketchy websites, and you can encourage strong passwords that are changed every 90 days. Show your employees what common scams look like and give them the knowledge they need to prevent an attack.
IT Secure Services offers a unique solution, using “…many lines of defense, from Dark Web monitoring to advanced AI software behavior detection.” By taking this approach you can protect your organization on multiple fronts.
Cloud Hosting as a Security Measure
Another approach you can take to protect your data is by moving it into the Cloud. This keeps vulnerable data off of your servers and safely hosted on a secure Cloud network. PiF offers secure Cloud hosting through Amazon Web Services (AWS), one of the largest providers of Cloud computing services in the world with over 90% of Fortune 100 companies working with an AWS Partner.
Unlike other cloud providers who define a region as a single data center, AWS Regions consist of multiple Availability Zones consisting of discrete data centers with identical power, networking, and connectivity abilities, and each housed in separate facilities to ensure the cloud is always secure. This means that even if one data center is compromised, your data is backed up to other data centers and still protected.
Hosting data on the Cloud or in a hybrid model is a simple way to keep your data safe.
What are the next steps you need to take?
Learning about Ransomware attacks can leave you feeling stressed and hopeless, but rather than ignoring the problem or hoping that your organization won’t be affected, taking action now can make you feel safe and confident in the long-term.
Reviewing your current security infrastructure is the first step you need to take in preventing a future attack. IT Secure Services can complete a comprehensive audit of the current state of security for your organization and help you stay protected in the future.
If secure Cloud hosting is a logical path forward for your organization, the first step in moving to the Cloud is consulting with us, as an Amazon Web Services partner we’ll help walk you through the process and identify next steps. We then identify the first workload to start testing in the cloud, focusing on dev/test, website and non-production servers as a first project. We’ll install the AWS Application Discovery Service on some of your on-premise servers to collect statistics which then will allow us to determine approximate costs and total cost of ownership.
We’d love to help you discover how AWS can protect your organization and simplify storing your data. Schedule a demo with us to have a conversation about your needs and how PiF can help.








